
In the rapidly evolving landscape of cybersecurity, businesses are faced with an exponentially increasing number of cyberthreats. One of the key battlegrounds in this digital war is the endpoint, the point at which a user’s device connects to a network. Endpoint security plays a crucial role in protecting business operations and sensitive data. In this guide, we’ll dive into the nuances of endpoint security, shedding light on its significance, essential components, best practices and challenges picking the best solution.
The Significance of Endpoint Security
One of the most vulnerable elements of a business network is something business professionals often overlook: endpoint devices which include devices such as laptops, desktops, smartphones, and tablets. These devices are not only the tools employees use to perform their tasks but are also potential vulnerabilities that cybercriminals exploit. A breach at the endpoint can lead to unauthorized access, data loss, and even compromise the entire network.
Endpoint security is, therefore, the practice of securing these entry points to ensure that each device connecting to the network is free from malicious threats. It goes beyond traditional antivirus solutions and aims to protect against a broad spectrum of cyber threats, including malware, ransomware, phishing attacks, and zero-day exploits. Let us look at what are the key components of endpoint security and best practices to follow when deploying them.
6 Key Components of Endpoint Security
1) Antivirus and Anti-Malware Solutions:
Traditional yet indispensable, the primary function of the antivirus software is to detect, quarantine, and eliminate malicious software—commonly known as viruses—that may attempt to compromise the security of endpoint devices. Anti-malware solutions complement this by identifying and eliminating various types of malicious software. While antivirus tools focus primarily on traditional viruses, anti-malware solutions cast a wider net, encompassing various types of malicious software. This includes trojans, worms, spyware, and other forms of malware that might slip through the cracks of traditional antivirus defenses.
2) Firewalls:
Firewalls act as a barrier between an internal network and external threats. They monitor and control incoming and outgoing network traffic based on predetermined security rules, preventing unauthorized access. This is crucial in thwarting potential cyber threats attempting to exploit vulnerabilities in the network.
Modern firewalls go beyond simply inspecting network packets. They have the capability to identify and control specific applications and services, allowing businesses to manage and regulate the types of software that can communicate with the network. Firewalls act as gatekeepers, blocking the execution of potentially harmful code. This is particularly crucial in preventing malware and other malicious software from infiltrating endpoint devices and compromising their integrity.
3) Endpoint Detection And Response (EDR):
Endpoint Detection and Response (EDR) emerges as a strategic and indispensable component in the arsenal of endpoint security, offering businesses heightened capabilities to detect, respond, and mitigate advanced cyber threats. EDR solutions operate on a continuous monitoring basis, keeping a watchful eye on endpoint activities in real time.
This continuous scrutiny enables the early detection of unusual behaviors or potential security incidents, reducing the time it takes to identify and respond to threats. EDR, with its behavioral analysis and threat hunting capabilities, excels in identifying and mitigating emerging threats by extending proactive defense not just against basic threats but also against Zero Day Threats and Advanced Persistent Threats (APTs).
4) Device Control:
Device control is a crucial component of endpoint security, contributing significantly to the overall protection of an organization’s network and sensitive data. Endpoint security focuses on securing individual devices (endpoints) like computers, laptops, mobile devices, and servers. Device control helps prevent unauthorized data transfer to external storage devices such as USB drives or external hard disks. This is crucial in protecting sensitive data from being accidentally or maliciously copied and taken out of the organization.
Employees or insiders with malicious intent may use external devices to transfer confidential information. Device control ensures that only authorized devices can be connected to the network, reducing the risk of insider threats and minimizing the attack surface by controlling the number of potential entry points for attackers.
5) Patch Management:
Regularly updating and patching software is crucial to closing vulnerabilities that cybercriminals may exploit. Endpoint security solutions often include patch management features to streamline this process. Patch management involves the systematic and timely application of updates and patches to software, operating systems, and applications. These updates are released by vendors to address known vulnerabilities and enhance the security of the software. Cybercriminals often target unpatched vulnerabilities in software to infiltrate systems. Patch management, by ensuring the prompt application of updates, minimizes the window of opportunity for cybercriminals to exploit these unknown vulnerabilities. Additionally, managing patches plays a crucial role in maintaining compliance with regulatory requirements, reducing the risk of legal consequences and financial penalties.
6) Data Encryption:
Data encryption plays a pivotal role in fortifying endpoint security, providing a robust layer of protection for sensitive information as it travels between devices and across networks. In the corporate landscape, where data breaches pose significant risks to businesses, encryption stands as a fundamental safeguard against unauthorized access, ensuring the confidentiality and integrity of valuable data.
In the digital era, where data is a valuable asset and cyber threats are pervasive, the importance of data encryption for endpoint security cannot be overstated. It serves as a foundational pillar in safeguarding sensitive information, meeting regulatory standards, and bolstering overall cybersecurity resilience. As businesses continue to navigate the complex landscape of digital risks, implementing and maintaining robust data encryption practices remains a fundamental strategy for ensuring the confidentiality and integrity of critical data assets.
6 Key Challenges with Endpoint Security
While endpoint security is paramount, businesses face several challenges in deploying effective, robust and sustainable endpoint security measures. It is imperative to evaluate the costs of having secure endpoints and the costs of having insecure endpoints.
1) Diverse and Dynamic IT Environments:
One of the primary challenges in deploying endpoint security is the diversity and dynamism of modern IT environments. Organizations often operate with a lack of cross platform functionality of devices, operating systems, and applications. Compatibility issues can arise when trying to implement a one-size-fits-all security solution, leading to gaps in protection. Achieving seamless integration across a heterogeneous IT landscape requires careful planning and consideration of diverse endpoint configurations. A Managed Services Provider (MSP) can guide you to make the best possible decision for your business.
2) User Resistance and Productivity Concerns:
Introducing new security measures can be met with resistance from end-users, especially if it affects their usual workflows or imposes additional steps for authentication. Balancing security needs with user productivity is a delicate task. Organizations must invest in user education and communicate the benefits of enhanced security measures to mitigate resistance. Striking a harmonious balance between robust security and user-friendly experiences is crucial for successful deployment.
3) Patch Management Challenges:
Regular software updates and patches are vital for addressing vulnerabilities and maintaining a secure endpoint environment. However, managing these updates across a large number of devices can be challenging. Ensuring timely and uniform application of patches requires robust patch management processes and tools. Failure to address this challenge leaves endpoints susceptible to exploitation by cybercriminals leveraging known vulnerabilities.
4) Scalability Concerns:
The scalability of endpoint security solutions is a significant consideration for growing organizations. As the number of endpoints increases, the security infrastructure must scale seamlessly to provide consistent protection. Deploying solutions that can efficiently scale without compromising performance is essential to accommodate the dynamic nature of business expansion.
5) Threat Evolution And Advanced Attacks:
Cyber threats are continually evolving, with adversaries employing increasingly sophisticated tactics. Traditional endpoint security measures may struggle to keep pace with these advanced attacks. Deploying solutions with advanced threat detection capabilities, such as machine learning and behavioral analysis, becomes crucial to effectively combat emerging threats and sophisticated attack vectors.
6) Budgetary Constraints:
Deploying comprehensive endpoint security solutions often requires a significant financial investment. Small and medium-sized enterprises, in particular, may face budgetary constraints that limit their ability to implement advanced security measures. Striking a balance between cost-effective solutions and robust security becomes crucial, requiring organizations to prioritize their most critical security needs within budgetary constraints.
Overcoming Challenges for Resilient Endpoint Security
Deploying effective endpoint security solutions is a complex undertaking, rife with challenges ranging from technical complexities to user resistance and budget limitations. Overcoming these challenges demands a strategic and holistic approach, including careful planning, user education, and investment in advanced technologies.
Organizations that navigate these hurdles successfully can establish a resilient security posture, safeguarding their endpoints against the ever-evolving landscape of cyber threats. As the threat landscape continues to evolve, addressing these challenges becomes not just a necessity but a strategic imperative for organizations committed to protecting their digital assets and ensuring the integrity of their operations.
Best Practices For Deploying Endpoint Security
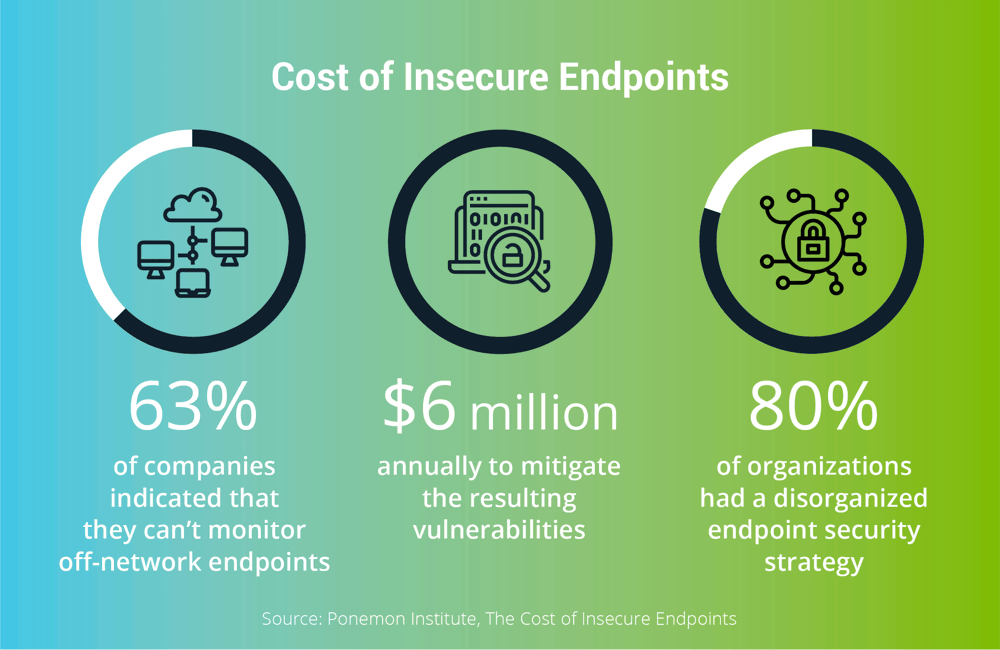
Endpoint security is paramount in the face of evolving cyber threats. It is important to evaluate the cost of deploying secure endpoints and the risk of deploying insecure endpoints. Either way, it is important to embrace best practices like regular software updates, enforcing strong access controls, and implementing multi-factor authentication. Leverage Endpoint Detection and Response (EDR) solutions for real-time monitoring and swift incident response and deploy patch management tools to help keep your systems up to date and compliant.
Encrypt sensitive data to add an extra layer of protection, and educate users on cybersecurity awareness. Network segmentation with the help of a firewall and Mobile Device Management (MDM) further fortify your defense. By adopting these practices, businesses can proactively safeguard endpoints, ensuring the resilience and security of their digital infrastructure.


